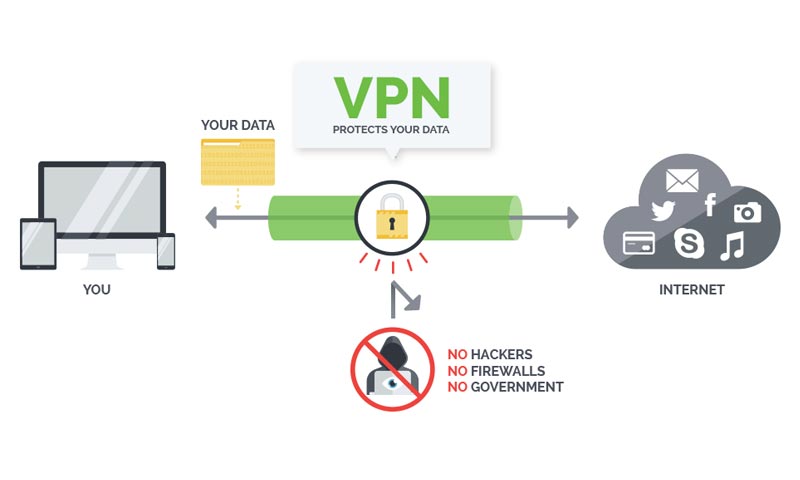
Since both VPN and proxy technologies will keep you unknown by keeping your IP address hidden, they operate in quite separate ways. A proxy works as a doorway to the software you are utilizing it in such as your ISP is basically your doorway to the web, a similar idea for the proxy to the software you use, proxies (other than SSH proxies) have not been encrypted but traffic will not be reaching your network, to start with.
An unknown VPN will secure your whole web connection the minute you interface with it, masking your utilization of everything from Utorrent to email to fundamental web browsing by building up a virtual network by means of our servers to reroute all the traffic and DNS.
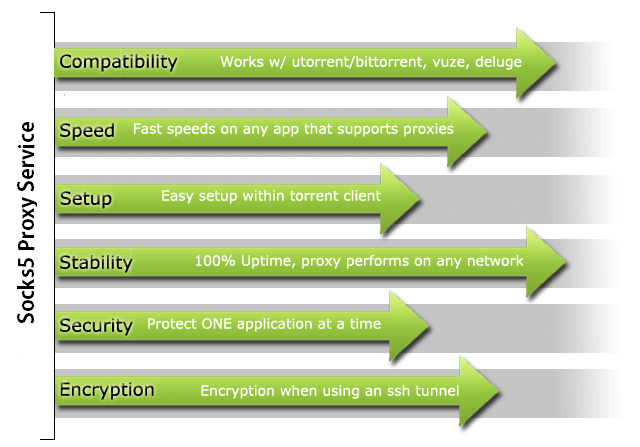
Take a proxy server just like a doorway. You are able to control your proxy settings, which will only be affecting your clients on torrent (Utorrent, Vuze, BitTorrent, etc.) or any different program which will help in supporting socks5 proxies. A proxy just helps in providing you with IP masking, although, to one application at a single moment.
When you are downloading and seeding torrents or when you are browsing the web, all of your traffic gets routed via an anonymous proxy server and gets directly sent to you. This points out that, in the torrent swarm, peers will not be able to find out your IP address, instead of TorGuard’s proxy server’s IP address. So when you are utilizing a torrent proxy, you will be able to get all the torrenting benefits as well as the proxy server, which includes speed, security, geographic location, an anonymous IP, and so on.
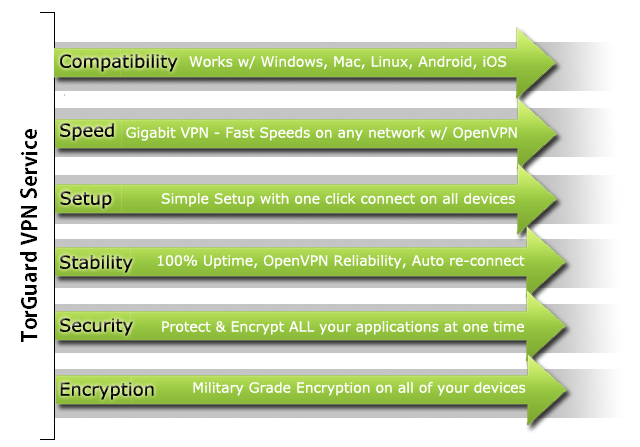
In contrast to a proxy, which just verifies your customer on torrent or internet browser, tunneling that is VPN (Virtual Private Network) encrypted verify 100% of all your web access, swapping your nearby ISP that routes for all of the applications. With a completely mysterious VPN server, you will appreciate upgraded security paying little respect to a geographic area.
This ensures your downloads on torrent as well as all other activity online or projects, for example, your internet browser, email, and some various third-party applications that associate with the web. You’ll additionally get quicker connections and military-grade encryption when utilizing a VPN, for example, TorGuard. Also, your VPN can without much of a stretch be connected or detached with only one click using a mouse.
Table of Contents
VPN vs. Proxy – Difference between a VPN and a Proxy

When it comes to a proxy, it helps you in connecting to a remote PC; however, a VPN again helps you in connecting to a remote PC. Well, this means they will be, more or less, one and the same thing, right? Well, not really. They might look similar, but they aren’t.
Let’s take an in-depth view of when you may like to use any of both of them, and why proxies could prove to be a poor substitute for VPNs.
Choosing the Right Tool Is Important
For all intents and purposes each other week there’s noteworthy news about encryption, snooping, leaked data or other concerns related to digital privacy. A large number of these articles talk about the significance of reinforcing the security of your Internet connection, such as utilizing a VPN (Virtual Private Network) when you’re using a café Wi-Fi or at a public area, yet they’re quite light when it comes to details.
How precisely do these proxy servers as well as the VPN connections we continue finding out about really work? In the case, if you will put the time and vitality in improving security you need to make certain you’re choosing the correct tool for the correct activity.
Despite the fact that they are unique on a fundamental level, Proxies and VPNs have been found to share one thing practically speaking: the two of them enable you to show up as though you are connecting with the web from another place. However, how they get to achieve this task and how much they offer encryption, protection, and different functions, fluctuates uncontrollably.
Proxies Keep Your IP Address Hidden
A proxy server is a server that goes about as a middle person in the progression of your web traffic with the goal that the activities on your web look like they have originated from elsewhere. Suppose for instance you are physically situated in New York City and you need to sign-in into a site that is geologically confined to just individuals situated in the United Kingdom. You will be able to interface with a proxy server which is basically situated inside the United Kingdom, at that point connect with that site.
The traffic from your internet browser would seem to begin from the remote PC and not from the one that you own. Proxys are extraordinary for low-stakes works, for example, watching YouTube videos that are region-restricted, to bypass simple content filters, or to bypass restrictions on services that are IP-based. In order to take an example, an online game is played by a lot of individuals in our family and here you earn a daily in-game bonus, on a server ranking website, when you vote for the game server.
However, the ranking site comes with a policy of one-vote-per-IP paying little respect to whether separate player names have been utilized. Well, thanks to these proxy servers as on account of proxy servers, every individual can put their vote and get their hands on the in-game bonus as a matter of the fact that every individual’s internet browser looks like being originating from an alternate IP address.
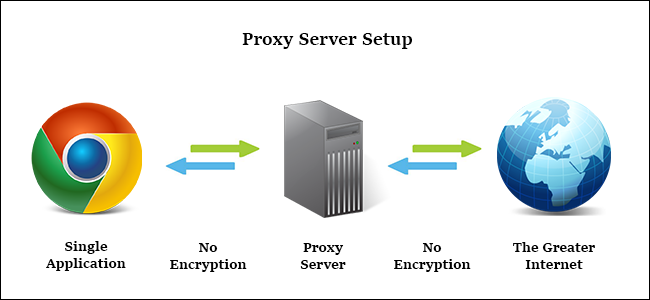
Moreover, if we see on the opposite side of these things, the proxy servers are not all that good for the tasks that involve high-stakes. The proxy servers only hide your IP address and go about as an idiotic man-in-the-middle for the Internet traffic that you have got. They are not encoding your traffic between your PC as well as the proxy server, they don’t normally take away identifying data or any sort of information from the transmissions past the simple IP swap, and there are no extra built-in protection or security preferences.
Anybody that has got the access to the stream of information or data (your government, your ISP, a person sniffing the Wi-Fi traffic at an airport, and so on.) is able to snoop on the traffic that you get. Further, certain adventures, for example, JavaScript elements or malicious Flash in your internet browser, can uncover your actual personality. This further makes proxy servers unacceptable for genuine and real tasks such as preventing the malicious Wi-FI hotspot administrator from taking your information.
The proxy server connections, at last, get configured on an application-by-application premise, not PC wide. You just aren’t configuring your whole PC in order to connect with the proxy–you configure your BitTorrent client, your internet browser, or any other application that is compatible with proxy.
This is extraordinary in the case if you simply need one application in order to interface with the proxy (like we previously mentioned above voting scheme) yet not all that good in the case if you wish to direct your whole web connection once again. Moreover, HTTP and SOCKS are the two most used and preferred proxy server protocols.
HTTP Proxies
The most primeval sort of proxy server, HTTP proxies are structured explicitly for primeval traffic. You just plug the proxy server into the configuration file of your internet browser (or utilize a browser extension in the case if your browser isn’t natively supporting proxies) and all your web traffic is directed via the remote proxy.
In the case, if you’re utilizing an HTTP proxy in order to interface with any kind of sensitive service, similar to your email or bank, it is critical for you to utilize an SSL enabled browser, and to also connect with a site, which basically supports an SSL encryption. As we have mentioned above, proxies aren’t into encoding any traffic, so the main encryption you get when utilizing them is simply the encryption you give.
SOCKS Proxies
When it comes to the proxy system called SOCKS, it is a valuable extension of the HTTP proxy system in that SOCKS is unconcerned with the sort of traffic that goes through it. On the one side, where HTTP proxies can just deal with web traffic, when it comes to the SOCKS server, it will basically go along any traffic it gets, regardless of whether that traffic is for a web server, an FTP server, or BitTorrent client.
In reality, in our article on securing the BitTorrent traffic, we suggest the utilization of BTGuard, an anonymizing SOCKS proxy service which is based out of Canada. The drawback to SOCKS proxies is that they are slower than HTTP proxies since they have all the more overhead and, similar to HTTP proxies, they offer no encryption past what you by and by applying to the provided connection.
How to Choose a Proxy?
With regards to choosing a proxy, it pays to… well, pay. While the Internet is flooded with a huge number of free proxy servers, they are nearly universally flaky with bad uptime. Those sorts of services may be extraordinary for a coincidental undertaking that takes a couple of minutes (and isn’t especially delicate in nature), however, it’s truly not worth depending on free proxies of obscure source for much else significant than that.
In the case, if you realize what you’re getting into as far as quality and security, you can discover heaps of free proxy servers at Proxy4Free, which is a very well entrenched free-proxy database.
While there is the possibility of stand-alone commercial services out there, for example, aforementioned BTGuard, the rise of PCs that are fast and cell phones combined with quicker connections (the two of which decrease the effect of encryption overhead) the proxy has to a great extent dropped out of support as an ever-increasing number of individuals pick to utilize superior VPN solutions.
Virtual Private Networks (VPN) Encrypt the Connection
Virtual Private Networks, similar to proxies, make your traffic show up as though it originates from a remote IP address. In any case, that is the place the similarities are put to an end. VPNs have been built up at the operating system level, and the VPN connection catches the whole network connection of the gadget it is configured on.
This implies dissimilar to a proxy server, which basically goes about as a man-in-the-middle server for one application (such as your internet browser or BitTorrent client), VPNs will catch the traffic of each and every application on your PC, from your internet browser to your web-based and online games to even Windows Update running out of sight in the background.
Moreover, this whole procedure is altogether gone through a vigorously encrypted passage between your remote network and your PC. This allows a VPN connection to be the best answer for any kind of high-stakes network to utilize where privacy protection or security is a worry. With the use of the VPN, neither your ISP nor some other snooping parties can get to the transmission between your PC and the VPN server.
In the case, for example, if you were going in a separate country, and you were stressed over signing into your monetary sites, email, or notwithstanding connecting securely to your home system from a far distance, you could without much of a stretch arrange your PC to utilize a VPN.
Regardless of whether you’re not as of now on a business tour in rural Africa, you can at present profit by utilizing a VPN. With a VPN that is enabled, you never need to stress over awful Wi-Fi/organize security rehearses at coffeehouses or that the free web at your inn is loaded with security holes. As a matter of fact, VPNs are incredible; they are not without their drawbacks. What you get in entire connection encryption, you pay for in cash and computing power.
Running a VPN requires great equipment and, accordingly, great VPN services are not provided free of cost (albeit a few suppliers, like TunnelBear, do offer an extremely simple free pack). Hope to pay in any event a couple of dollars a month for a strong VPN service such as the solutions we suggest in our VPN guide, StrongVPN, and ExpressVPN.
Another cost that has been associated with a VPN is its performance. Proxy servers simply help in passing your information or data along. There is no cost related to bandwidth and only some extra latency while you are using them. Moreover, on the other hand, VPN servers, eat up both bandwidth and processing power on account of the overhead which has been introduced via encryption protocols.
However better the VPN protocol as well as the remote hardware, lesser the overhead is there. The selection process of a VPN is quite more nuanced as compared to selecting a free of cost proxy server. In the case, if you are in a hurry and you are asking for a VPN service you can rely upon, which we both highly suggest as well as utilize ourselves on a regular basis, we will take you to the Strong VPN as our VPN preferred by us.
In the end, proxies are good in order to hide your identity while doing trivial tasks (such as “sneaking” into some different country in order to see a sports match), however, when it’s about more serious tasks (such as protecting or to secure yourself from snooping) you no doubt have to have a VPN.