Getting a PC infection has happened to numerous clients in some manner or another. To most, it is just a mellow bother, requiring a clean-up and after that introducing that antivirus program that you’ve been importance to introduce yet never got around to. Be that as it may, in different cases, it very well may be a finished calamity, with your PC transforming into an over the top expensive block which no measure of antivirus can ensure.
In this rundown, we will feature a portion of the most exceedingly terrible and infamous PC infections that have caused a great deal of harm, all things considered. What’s more, since individuals more often than not compare general malware like worms and trojan ponies as infections, we’re including them also.
This malware has caused huge damage, adding up to billions of dollars and disturbing basic genuine framework. What amount of harm can an infection truly cause? Do programmers truly take information and characters and wreck PCs? Well, here we have the 10 best antivirus programmes along with the names of computer viruses, in order to have an in-depth awareness about all of these concerns.
Table of Contents
Top 10 Most-Known Malicious Computer Viruses
1. CryptoLocker
With regards to malware, ransomware is the newcomer. While a great many people can shake off names like ‘Trojan’, ‘infections’, and ‘spyware’, they’re regularly not very acquainted with ransomware. Ransomware is a sort of malware that kidnaps your records.
You know in heist motion pictures when the trouble maker snatches somebody and undermines them as a byproduct of cash? Ransomware works much like that, with the exception of your PC is abducted by an anonymous trouble maker.
Discharged in September 2013, CryptoLocker spread through email connections and scrambled the client’s records with the goal that they couldn’t get to them. The programmers at that point sent a decoding key as an end-result of a whole of cash, as a rule someplace from a couple of hundred pounds up to a few fantastic.
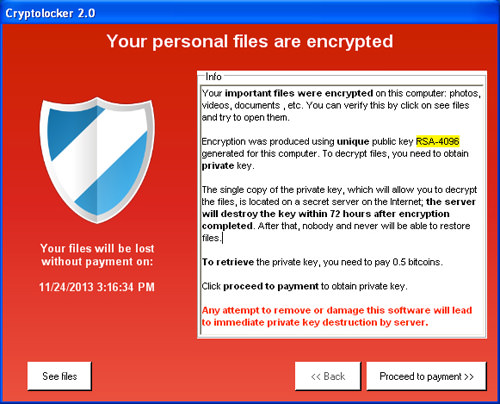
With a portion of the hacking endeavors, System Restore or recuperation programming worked. In spite of the fact that with a significant number of the tainted PCs, if the unfortunate casualties didn’t pay up they’d lose every one of their documents. Presently is a decent time to remind you to constantly back your documents up!
In June 2014, Operation Tovar brought down Evgeniy Bogachev, the pioneer of the group of programmers behind CryptoLocker. In February, the FBI offered a cool $3 million reward for Bogachev.
Cost of the malware: With 500,000 unfortunate casualties, CryptoLocker made upwards of $30 million of every 100 days.
2. ILOVEYOU
While ILOVEYOU sounds like a merry bon saying you may discover imprinted within a Valentine’s Day card, it’s in reality far, definitely viler than that. ILOVEYOU is a standout amongst the most outstanding and damaging infections ever.
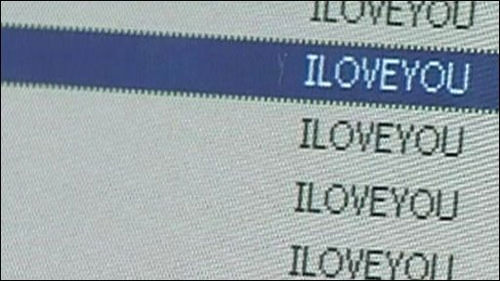
It’s been a long time since ILOVEYOU was let free on the web. By the present norms, it’s a truly manageable infection, yet in 2000 it was the most harming malware occasion ever. Likely, ILOVEYOU enlivened numerous programmers to employ their console as a weapon.

Yet, for what reason would it say it was so merciless?
All things considered, in 2000 malware was somewhat of a fantasy. Truth be told, it was such a legend, that malware could pull off being totally unsubtle. On the off chance that you got an email today like the one that was sent around in 2000, you’d never open it. (We trust!) The infection arrived in an email with a title that said: “I cherish you”.
Being interested sorts, individuals clicked into the email easily—paying little respect to the reality the email wasn’t from anybody they knew. The malware was a worm that was downloaded by tapping on a connection called ‘LOVE-LETTER-FOR-YOU.TXT.vbs’.
ILOVEYOU overwrote framework documents and individual records and spread itself again and again and over once more. ILOVEYOU hit headlines around the world and still individuals tapped on the content—possibly to test that it truly was as terrible as it should be, jabbing the hold on for a stick, to utilize an allegory.
ILOVEYOU was so viable it really held the Guinness World Record as the most ‘harmful’ infection ever, a viral infection, apparently. Two youthful Filipino developers, Reonel Ramones, and Onel de Guzman were named as the culprits but since there were no laws against composing malware, their case was dropped and they went free.
Cost of the malware: $15 billion.
3. MyDoom
MyDoom is viewed as the most harming infection at any point discharged—and with a name like MyDoom would you expect anything less?
MyDoom, as ILOVEYOU, is a record-holder and was the quickest spreading email-based worm ever. MyDoom was an odd one, as it hit tech organizations like SCO, Microsoft, and Google with a Distributed Denial of Service assault (25% of contaminated hosts of them). An adaptation of the infection purportedly hit the SCO site with a boatload of traffic trying to crash its servers.

Just as focusing on tech organizations, MyDoom spammed garbage mail through tainted PCs, with the content that said “andy; I’m simply carrying out my responsibility, not all that much, sorry”. Who was Andy? Who knows? In 2004, generally somewhere close to 16-25% of the sum total of what messages had been tainted by MyDoom.
Cost of the malware: $38 billion.
4. Tempest Worm
Tempest Worm was an especially horrendous infection that made the rounds in 2006 with a headline of ‘230 dead as tempest players Europe’.
Interested, individuals would open the email and snap on a connection to the news story and that is the point at which the issues began. Tempest Worm was a Trojan steed that tainted PCs, here and there transforming them into zombies or bots to proceed with the spread of the infection and to send a gigantic measure of spam mail.
Tip: never open a connection in an email except if you know precisely what it is.
By July 2007, Storm Worm was gotten in excess of 200 million messages.
Cost of the malware: A careful expense is yet to be determined.
5. Sasser and Netsky
17-year-old Sven Jaschan made Sasser and Netsky, two worms, in the early noughties. Sasser and Netsky are really two separate worms, yet they’re regularly gathered in light of the fact that the likenesses in the code persuaded they were made by a similar individual.
Sasser spread through contaminated PCs by filtering irregular IP delivers and teaching them to download the infection. Netsky was the more natural email-based worm. Netsky was really the more popular infection and caused a gigantic measure of issues in 2004.
A German understudy, Jaschan was captured when various tip-offs were accounted for to the police. The theory proposed Jaschan had really composed the infections to make business for his mom and stepfather’s PC business. Since he was under 18 when he composed the infection, Jaschan spent his jail sentence on post-trial supervision.
Significantly all the more fascinating is Jaschan’s inspiration. MyDoom was spreading quickly at the time and Jaschan, an amateur coder, needed to perceive what might occur if his bug could spread quicker than MyDoom. Things immediately heightened from that point.
Sasser was so viable it really ground 33% of the post workplaces in Taiwan to a stop, shut down 130 parts of a Finnish bank, and constrained rail and transoceanic flights to be dropped.
Cost of malware: Around $31 billion.
6. Anna Kournikova
What’s a tennis player got the opportunity to do with a rundown of intriguing infections? A considerable amount, as it so occurs. We will get this off the beaten path first: the Anna Kournikova infection is truly agreeable contrasted with numerous on the rundown.
So, in the right on time to mid-noughties, Anna Kournikova was a standout amongst the most looked terms on the web. Individuals were only excited about tennis.
Jan De Wit, a 20-year-old Dutchman, composed the infection as ‘a joke’. The subject was “Here you have, ;0)” with a connected record called AnnaKournikova.jpg.vbs. Anna was entirely innocuous and didn’t do much real harm; however, De Wit transformed himself into police at any rate.
The city hall leader of the town approached and said the city ought to be pleased to have created such a gifted young fellow and offered him a vocation as a geek once he was done his training.
Cost of the malware: $166,000.
7. Code Red
Code Red originally surfaced in 2001 and was found by two eEye Digital Security workers. It was named Code Red on the grounds that the pair were drinking Code Red Mountain Dew at the season of revelation. The worm focused on PCs with Microsoft IIS web server introduced, misusing a cradle flood issue in the framework.
It leaves almost no follow on the hard plate as it can run altogether on memory, with a size of 3,569 bytes. When tainted, it will continue to make a hundred duplicates of itself yet because of a bug in the programming, it will copy considerably more and winds up eating a ton of the frameworks assets.
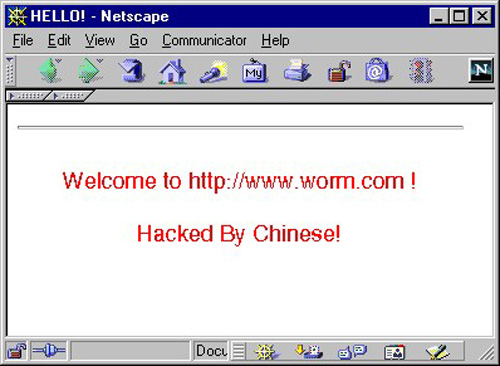
It will at that point dispatch a disavowal of administration assault on a few IP addresses, popular among them the site of the White House. It additionally permits secondary passage access to the server, taking into account remote access to the machine. The most critical side effect is the message it abandons on influenced site pages, “Hacked By Chinese!”, which has turned into an image itself.
A fix was later discharged and it was the gauge that it caused $2 billion in lost profitability. A sum of 1-2 million servers was influenced, which is astounding when you consider there were 6 million IIS servers at the time.
8. Melissa
Named after an outlandish artist from Florida, it was made by David L. Smith in 1999. It began as a contaminated Word archive that was posted up on the alt.sex Usenet gathering, professing to be a rundown of passwords for explicit locales.
This got individuals inquisitive and when it was downloaded and opened, it would trigger the full scale inside and release its payload.

The infection will mail itself to the main 50 individuals in the client’s email address book and this caused an expansion of email traffic, upsetting the email administrations of governments and companies. It likewise in some cases defiled archives by embeddings a Simpsons reference into them.
Smith was in the end gotten when they followed the Word record to him. The record was transferred utilizing a stolen AOL account and with their assistance, law implementation had the option to capture him not exactly seven days since the flare-up began.
He coordinated with the FBI in catching different infection makers, popular among them the maker of the Anna Kournikova infection. For his collaboration, he served just 20 months and paid a fine of $5000 of his multi-year sentence. The infection purportedly caused $80 million in harms.
9. Zeus
Zeus is a Trojan steed made to contaminate Windows PCs with the goal that it will perform different criminal errands. The most well-known of these assignments are normally man-in-the-program keylogging and structure getting. Most of the PCs were tainted either through drive-by downloads or phishing tricks.
First recognized in 2009, it figured out how to bargain a large number of FTP records and PCs from huge global enterprises and banks, for example, Amazon, Oracle, Bank of America, Cisco, and so on. Controllers of the Zeus botnet utilized it to take the login accreditations of informal community, email and banking accounts.
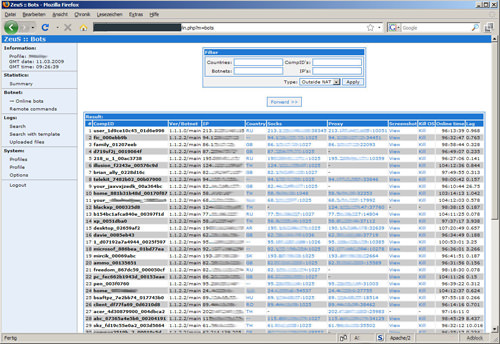
In only us, it was evaluated that more than 1 million PCs were contaminated, with 25% in the US. The whole activity was complex, including individuals from around the globe to go about as cash donkeys to sneak and exchange money to the instigators in Eastern Europe. About $70 million were stolen and possessing the ring.
100 individuals were captured in an association with the task. In late 2010, the maker of Zeus declared his retirement yet numerous specialists trust this to be false.
10. Conficker
Otherwise called Downup or Downadup, Conficker is a worm of obscure origin for Windows that showed up in 2008. The name comes to structure the English word, design and a German pejorative. It contaminates PCs utilizing defects in the OS to make a botnet.
The malware had the option to contaminate in excess of 9 million PCs all around the globe, influencing governments, organizations, and people. It was one of the biggest known worm diseases to ever surface causing gauge harm of $9 billion.
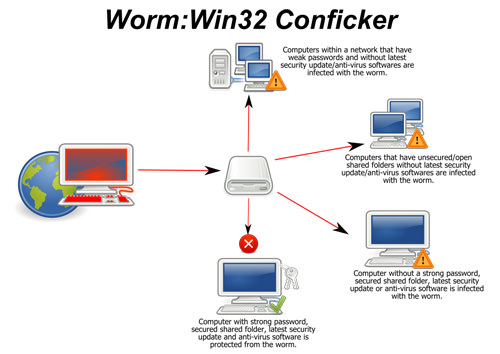
The worm works by abusing a system administration defenselessness that was available and unpatched in Windows. When contaminated, the worm will at that point reset account lockout strategies, square access to Windows update and antivirus destinations turn off specific administrations and lockout client accounts among many.
At that point, it continues to introduce programming that will transform the PC into a botnet slave and scareware to trick cash off the client. Microsoft later furnished a fix and fix with numerous antivirus merchants giving updates to their definitions.
So, there you have it: while infections and malware may appear as though a legend scrounged up by tech organizations, they are an undeniable danger that has caused billions in harm.
Moreover, there are ways of removing virus from your laptop without the use of any Antivirus, which we have discussed below.
How to Remove Virus from Laptop without Antivirus?
Being a computer program, a Virus has the ability to copy itself and infect PCs. Also, when it comes to referring other malware types, which includes adware, spyware programs, etc. (which doesn’t come with the ability to reproduce), the term “virus” is used erroneously.
Moreover, a true virus has an ability to spread from one PC to another (in a manner of the executable code). The most common way in which a virus infects a PC, however, is via USB/Flash drives Other than that, a few common viruses, for example, ‘Ravmon’, ‘New Folder.exe’, ‘Orkut has been banned’ spread via USB drive.
Most of the antivirus programs don’t have the ability to detect them and just in case, even if they are, they are not able to delete/remove the file, in most cases and they only quarantine it. So, today, here we would recommend command prompt in order to remove harmful files which couldn’t be removed by any anti-virus. Here is how:
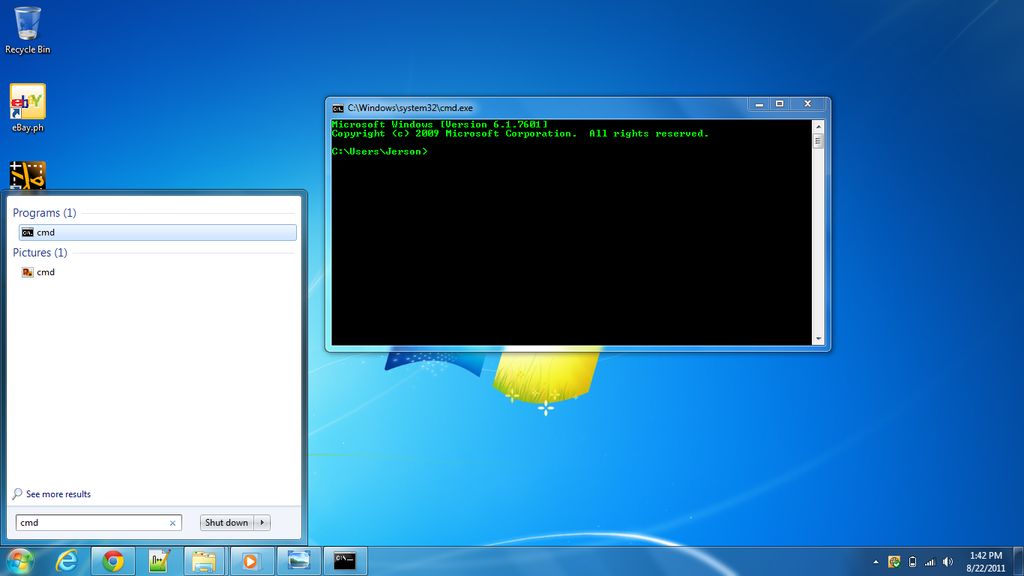
Step 1:
Simply Go to Start and Run the command prompt, and then type cmd in the search programs and files.
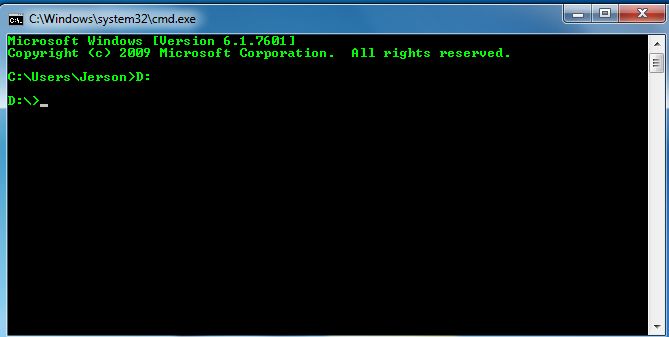
Step 2:
Now, Select the drive affected by the virus (drivename:)
Examples
- C:
- J:
- F:
- D:
- E:
Step 3:
- Type attrib –“s -h *.* /s /d” and then click “enter”
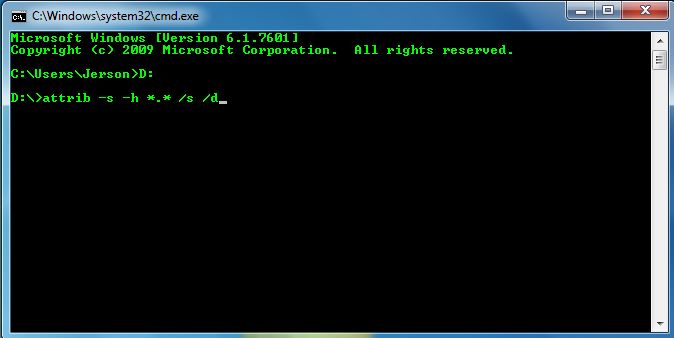
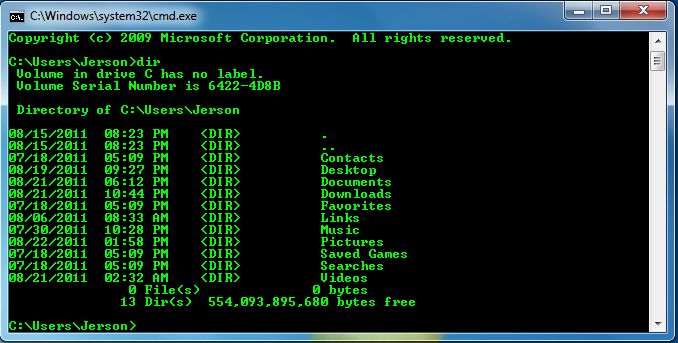
Step 4:
- Now, type “dir”
- The “dir” command will show you the drive’s content
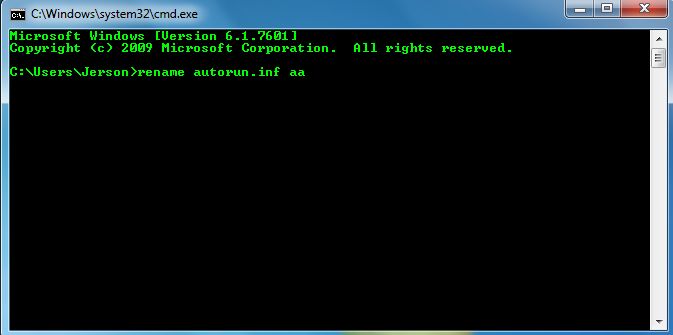
Step 5:
- Check for any “unusual .exe” file.
- If you find any “autorun.inf” file, go ahead and rename it.
- (rename filename.extension newfilename)
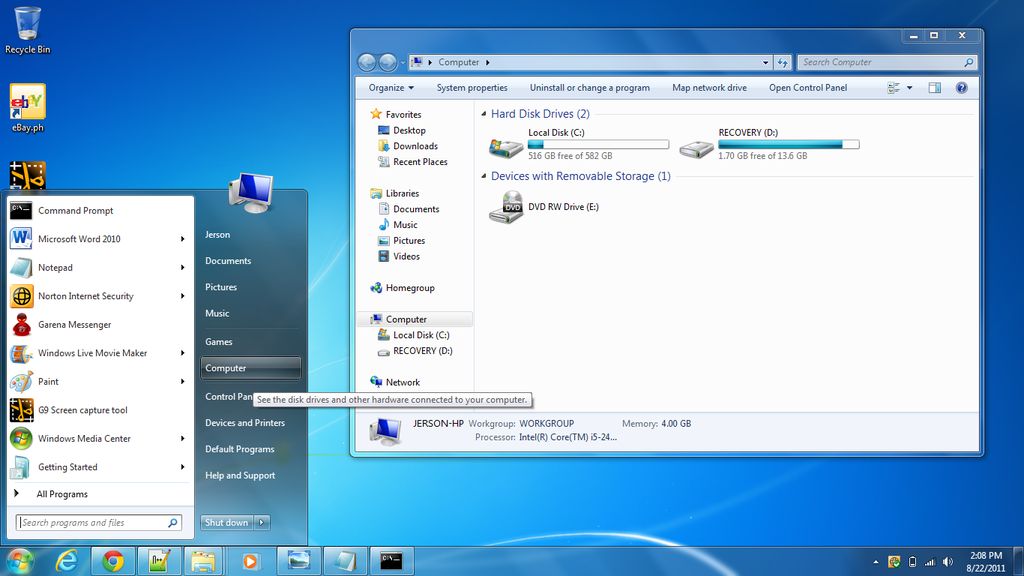
Step 6:
- By doing the following mentioned steps you will now be able to access the drive without affecting the virus
- Now, go to my computer
Step 7:
- Select the drive
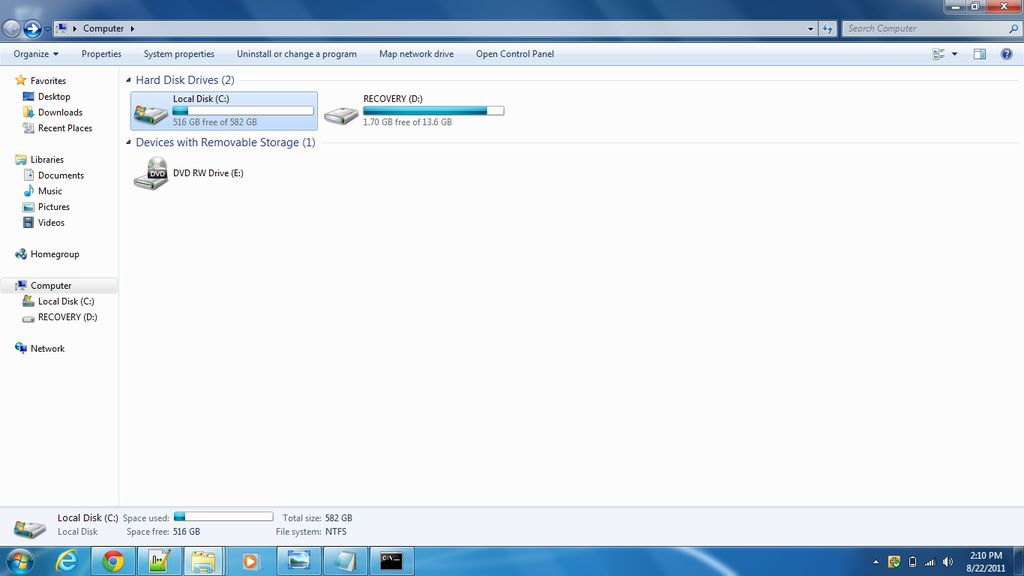
Step 8:
- Now, delete the files that are harmful
- *you can also remove/delete the harmful files by the use of command prompt
- (type del filename)
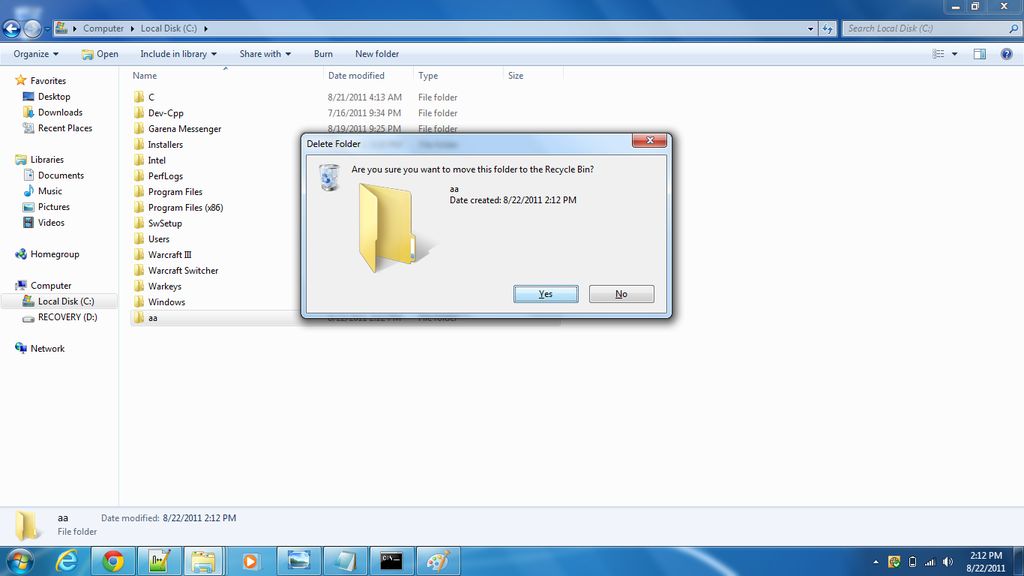
In the end, we hope the above-mentioned steps help you in dealing with these harmful viruses.
Until then!





